IDS
IDS, Intrusion Detection System, recognizes threats and movements within the network that may be an attack. Recognized threats are logged to the network administrator. Thus, threats in traffic are easily detected by IDS. IDS also performs in-depth packet analysis. Thus, it plays an important role in the early detection of a threat trying to break into or take over a system, or suspicious processes that may initiate a network or system attack. Packages identified as threats are marked.
IDS technology monitors network traffic and packets in traffic. The detection method used can be signature or anomaly-based. Certain patterns used to detect known attacks and respond to these threats with predefined actions are called “signatures”. Packet streams are compared against predefined signatures to see if there is a match. In this way, an alarm is generated for traffic outside the current rule list. An anomaly-based intrusion detection system, when an erroneous or abnormal situation is encountered, classifies it as an anomaly. Again, certain signatures can be used to control the nature of the behavior classified as an abnormality. IDS has an intelligent structure that constantly learns and improves itself.
IDS technology works with two different tools. These are the Network Sensor and Server Sensor tools. Network sensors listen and record network traffic. Packets presenting a dangerous situation are detected by network sensors. Packages that do not comply with the rule list are logged. Server sensors, on the other hand, only monitor the traffic coming to the server. Server and network sensors work the same and use the same database, the only difference being the domains they track.
IPS
IPS, on the other hand, Intrusion Prevention System is a security system used to prevent possible damage after detecting security breaches, harmful actions, or risky connections in the network. The IPS are usually located just behind the firewall or within the network with the firewall, between the outside world and the internal network. That is, it is placed in the direct communication path between the source and the destination. Packages are actively analyzed and predetermined actions are performed automatically. In this way, it creates an analysis layer for the network.
IPS products are often deployed at web gateways and operate without interrupting traffic. It controls the passing of malicious and harmless packets detected by IDS on incoming and outgoing network traffic. Threats detected by IDS are blocked with IPS based on a certain rule list. It reports these events to system administrators. It takes preventive actions such as shutting down access points and configuring the firewall to prevent future attacks.
The IPS operating structure is divided into three. Network-Based IPS, User-Based IPS, and Wireless Based IPS.
- Network-Based IPS: Systems that examine the traffic on the network by making protocol analysis.
- User-Based IPS: These are systems that aim to prevent attacks against the host computer with only IPS installed.
- Wireless Based IPS: Systems that detect suspicious movements by analyzing wireless network traffic and aim to prevent attack attempts.
The most important feature of IPS technology is that hardware-based IPS works without slowing down the system. IPS must work fast and synchronously to avoid attacks that degrade network performance by providing high throughput. The IPS device keeps itself up-to-date against attacks by downloading the database developed by the manufacturer against next-generation attacks. When a new unidentified network threat emerges, there is an opportunity for attackers to exploit the vulnerability before the security patch is applied. For this reason, IPS provides complete protection by preventing harmful traffic from entering the network in addition to IDS products. In this way, it prevents performance problems that may arise and gives successful results by working efficiently.
IDS vs IPS
IDS is a monitoring system while IPS is a control system. IDS cannot modify network packets, while IPS prevents the packet from being delivered from source to destination based on the packet’s contents, IP address, and the way it blocks traffic. IPS and IDS are used integrated with Firewall devices. Many Firewall devices can restrict the passage of packets in traffic, but cannot automatically reprogram themselves in case of an attack. With IPS and IDS, this situation is eliminated. Thanks to IDS technology, it can be detected that an attack has been carried out on the network that you want to protect. Thanks to IPS technology, the attacking source can be prevented from accessing the system.
Due to their nature, IDS and IPS are installed as Layer 2 but run on Layer 7. After the device is installed, it is run in “Learning” mode. In this process, the system/security manager and users act together and discuss the block or permission status of the package related to the threats that warn at certain periods in the traffic. As a result of the studies that lasted about two to three months, the signature sets for the traffic become clear. These signature sets are updated periodically to keep the system secure. In addition, these devices can be used by performing traffic monitoring (IDS) with a single cable and traffic domination (IPS) with a double cable, just like a HUB. Thus, in a simple sensor structure, the system can be easily controlled by acting as a single cable without affecting the traffic. In addition, a single device can be connected to multiple points and can be positioned at the desired point.
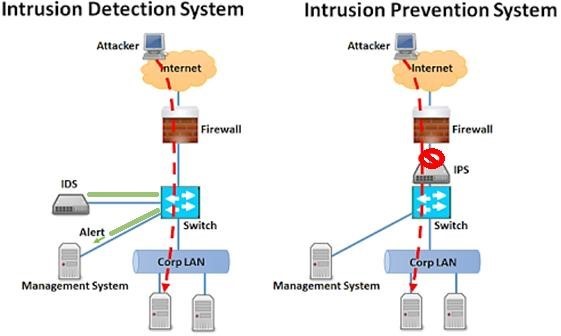
IDS and IPS read network packets and compare their contents against a database of known threats. The main difference between them is what happens next. IDS are detection and monitoring tools that do not act on their own. IPS is a control system that accepts or rejects a packet according to a set of rules. IDS does not take action on its own against the events it detects, but IPS can interfere with incoming/outgoing packets in network traffic based on predefined rules and action sets.
IPS and IDS play an important role when systems are configured correctly to detect, catch and prevent serious attacks. If IPS and IDS products are used together, they are defined as Intrusion Detection and Prevention Systems, or IDPS for short. In advanced systems, IPS and IDS are used together as an IDPS structure.
With the advancement of technology and the increase in the number and use of new applications, traditional Firewall devices have weakened in analyzing network traffic and keeping the network away from threats. At this point, new generation Firewall devices appear in an integrated structure with IDS and IPS technologies. In this way, Firewall devices play a much more effective role in traffic monitoring and management.
Some of the advantages of intrusion detection, analysis, and prevention systems are sending a warning to the security administrators who manage the system according to the level of the attack, detecting malicious software and disconnecting the connection resources before harming the system, dropping the packages that are found to be harmful, fixing CRC errors, software or user It is among the advantages of detecting possible attacks originating from the source, sending a warning to security managers about the subject, and keeping a record of past attack patterns in order to strengthen the defense.
However, the IDS and IPS structure has the potential to disrupt a user-friendly structure. As IPS and IDS are automated systems, they can produce contradictory results from time to time, no matter how well they are configured. In such a case, the user experience is negatively affected. To minimize this situation and ensure maximum security, both systems must be configured with the best settings and included in a long testing process. For this reason, IDS needs a human or software to review the results. IPS, on the other hand, needs a database containing threats and action orders, which must be kept up to date.
